
Utah Data Center
Background
The Utah Data Center, code-named Bumblehive, is the first Intelligence Community Comprehensive National Cyber-security Initiative (IC CNCI) data center designed to support the Intelligence Community's efforts to monitor, strengthen and protect the nation. NSA is the executive agent for the Office of the Director of National Intelligence (ODNI) and will be the lead agency at the center.The steady rise in available computer power and the development of novel computer platforms will enable us to easily turn the huge volume of incoming data into an asset to be exploited, for the good of the nation.

The Utah Data Center is currently under construction and is expected to open in October 2013. Our 1.5 billion-dollar one million square-foot Bluffdale / Camp Williams facility will house a 100,000 sq-ft mission critical data center. The remaining 900,000 SF will be used for technical support and administrative space. Other supporting facilities include water treatment facilities, chiller plant, power substations, vehicle inspection facility, visitor control center, and sixty diesel-fueled emergency standby generators and fuel facility for a 3-day 100% power backup capability.
Utah Data Center Site Plan
The site plan below shows the location of the administration building, chiller plant, data halls, generators, fuel storage tanks, storage warehouse, power substations, visitor control center, and vehicle inspection facility. View the full-size Utah Data Center Site Plan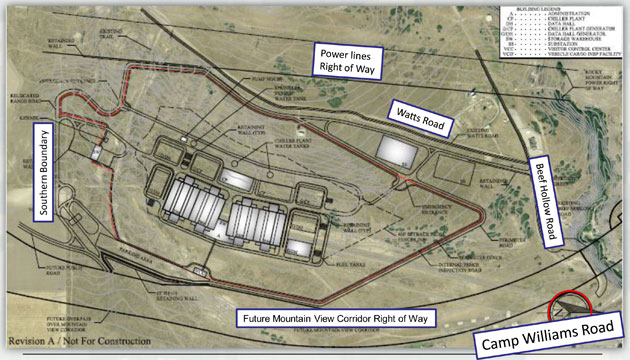
Utah Data Center Construction Photos
Here are some photos of the Utah Data Center under construction: March 2012
March 2012  July 2012
July 2012  July 2012
July 2012  October 2012
October 2012
Utah Data Center Technical Specifications
Data Storage Capacity
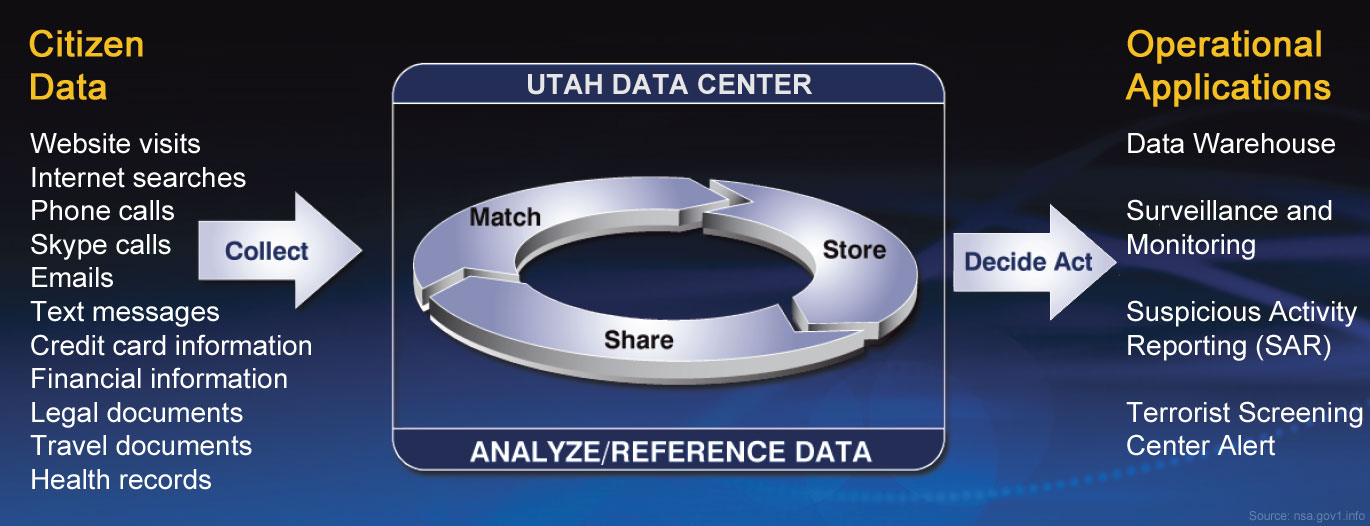
The storage capacity of the Utah Data Center will be measured in "zettabytes". What exactly is a zettabyte? There are a thousand gigabytes in a terabyte; a thousand terabytes in a petabyte; a thousand petabytes in an exabyte; and a thousand exabytes in a zettabyte. Some of our employees like to refer to them as "alottabytes".Learn more about the domestic surveillance data we plan to process and store in the Utah Data Center.
Code-Breaking Supercomputer Platform
In October 2012, the U.S. Department of Energy's (DOE) Oak Ridge National Laboratory launched the Titan Supercomputer, which is capable of churning through more than 20,000 trillion calculations each second or 20 petaflops. (1 petaflop = 1 quadrillion instructions per second).
Our Target: 256-bit AES
The Advanced Encryption Standard (AES) algorithm is used worldwide to encrypt electronic data on hard drives, email systems, and web browsers. The AES 256-bit encryption key is the standard for top-secret US government communications. Computer experts have estimated it would take longer than the age of the universe to break the code using a trial-and-error brute force attack with today's computing technology.In 2004, the NSA launched a plan to use the Multiprogram Research Facility in Oak Ridge, Tennessee to build a classified supercomputer designed specifically for cryptanalysis targeting the AES algorithm. Recently, our classified NSA Oak Ridge facility made a stunning breakthrough that is leading us on a path towards building the first exaflop machine (1 quintillion instructions per second) by 2018. This will give us the capability to break the AES encryption key within an actionable time period and allow us to read and process stored encrypted domestic data as well as foreign diplomatic and military communications.
 Visitor Control Center
Visitor Control Center
Construction Status
We're using a Critical Path Method (CPM) schedule to track the cost and resource data for over 26,000 activities. The project initially required over a million cubic yards of earthwork and nearly seven miles of new roadways. The massive twenty-building complex is being completed in three phases. The first phase was completed last Fall and includes the first of four data halls (Data Center Module DCM 1); the Administration Building; Data Center Loading and Storage; Chiller Plant #1 and storage tanks; Generator Plant #1 with fuel system storage; Visitor Control Center; Vehicle Cargo Inspection Facility; kennel; perimeter warehouse; and fire pump building.The second phase, completed early in 2013 includes the second data hall (DCM 2) along with Generator Plant #2 with fuel system storage.

The final phase is scheduled to be completed by October 2013 and includes the remaining two data halls (DCM 3 and 4); Generator Plants 3 and 4 with fuel system storage; and Chiller Plant #2 and storage tanks. Because of the national security implications of an on-time opening of this critical facility, the NSA has already begun the installation of classified equipment in the first two data halls (DCM 1 and 2).
 April 2013
April 2013


No comments:
Post a Comment